 |
E
and CapDesk |
The E platform uses capability-based security, which is a software architecture for achieving the Principle of Least Authority (POLA) in computer systems. POLA is a simple and timeless principle: never grant anyone or anything more authority than they require. This principle is referred to as “Need to Know” in classified information venues, and is known as the “valet key” when applied to standard automobiles: the valet key giving the valet only the authority required to drive the car, not the unneeded additional authority to open the trunk. This principle is known as “exact change” when purchasing milk at the local 7-11. The only people who have trouble understanding POLA are credit card companies (which really do tell you to hand all your credit to the unknown operator of a remote Web site), and computer security experts who tell you to use larger numbers of longer passwords and ever more complicated firewalls.
All Windows and Unix operating systems (referred to as “Winix” hereafter) utterly disregard the concept of POLA. When you launch any application—be it a $5000 version of AutoCAD fresh from the box or the Elf Bowling game downloaded from an unknown site on the Web—that application is immediately and automatically endowed with all the authority you yourself hold. Such applications can plant Trojans as part of your startup profile, read all your email, transmit themselves to everyone in your address book using your name, and can connect via TCP/IP to their remote masters for further instruction. This is, candidly, madness.
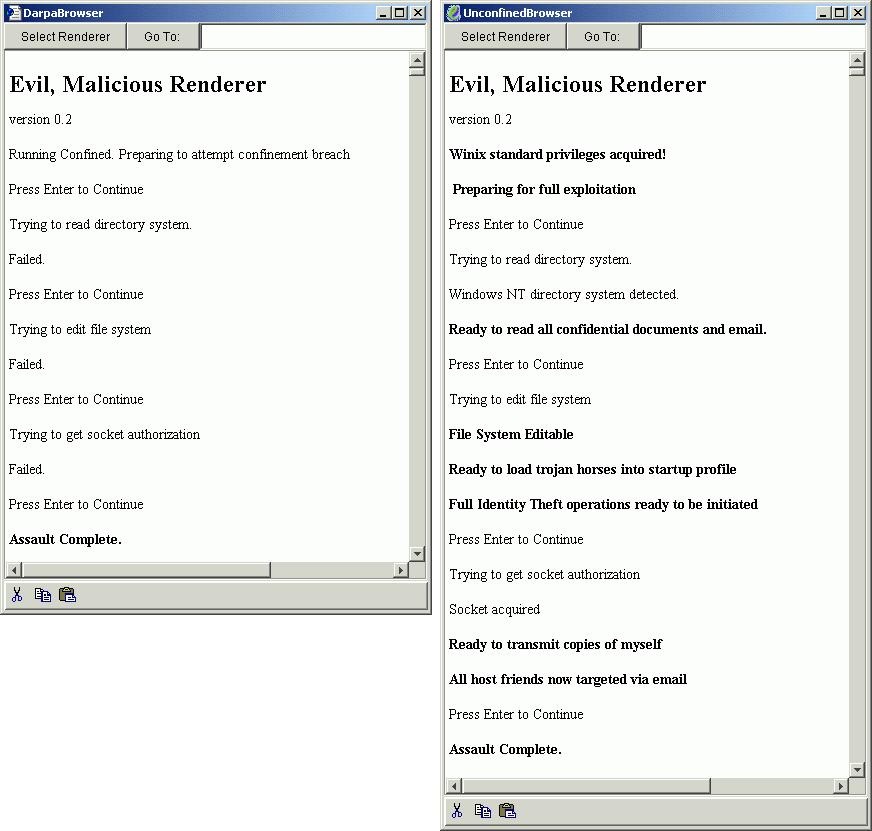
Side-by-Side comparison of a malicious Web Browser running under CapDesk capability confinement (left), versus the same Browser running with standard Windows/Unix privileges (right). The confined Browser fails in all attempts to suborn the computer; the Winix-enabled Browser takes full control.
With the E platform and the CapDesk capability secure desktop, software modules receive no authority by default. Programs started in strict confinement (a level of confinement far stricter than the confinement of the Java applet sandbox). They receive authority only through the actions of the user.
A traditional initial objection to this strategy is that the user would have to spend much of his time granting authorities. However, Combex has demonstrated with its existing operational prototypes that this does not need to be the case. Actual applications in the field require surprisingly few authorities, and standard software technologies, such as the File Open dialog box and the drag/drop metaphor, make natural vehicles for their conveyance. No passwords are required, no user authorization lists need management or maintenance. A production version of the CapDesk desktop would look and feel like Windows or KDE, yet would create a secure environment almost for free.
So dramatically different is security as supplied with the E platform, it turns the traditional wisdom, “You cannot have security without paying a price in flexibility” on its head, demonstrating that this dichotomy is only true when forced to use traditional security strategies.
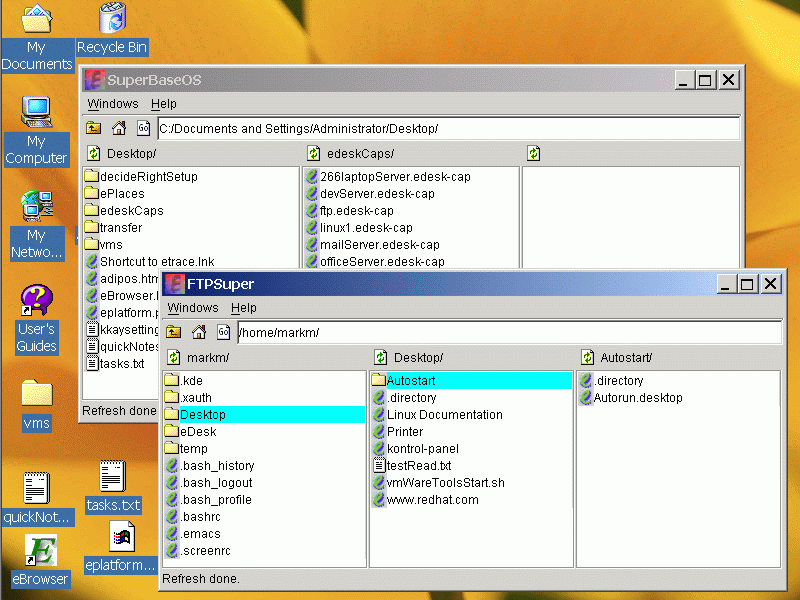
CapDesk running on Win2K with file manager windows open on the host OS and on a remote Linux system; the communication with the remote Linux system is capability secure and strongly encrypted. CapDesk blends functionality of the Microsoft File Explorer, FTP, SSH, and flexible fine grain security options in an integrated fashion not reproduced in any conventional application. The first operational version of CapDesk was developed by a single programmer over the course of a month of weekends—a remarkable comment on the productivity E provides for secure distributed systems.
The E platform enhances not only security of individual computers, but also the security, reliability, maintainability, and development speed of distributed systems. Peer-to-peer, B2B, and corporate intranet systems benefit from E’s deadlock-free promise-based distributed computing architecture, and from the way in which all communication is automatically and transparently strongly encrypted without programmer effort. The tutorial application for first-time learners of E is the eChat peer-to-peer capability secure chat tool, which is only five pages of code. Anecdotal evidence suggests that E can offer developers a productivity improvement somewhere between a factor of 3 and a factor of 7 over conventional programming languages such as Java, within the domain of secure distributed applications.